How to disable basic authentication in Office 365. There is more than one way to block basic authentication in Office 365 (Microsoft 365). For example, you can use: Security Defaults – turned on by default for all new tenants. This set of security-related settings disables all legacy authentication methods, including basic auth and app passwords. Hi Shawn Deng, Thanks for you reply. I have some more questions. As per the document - End of Support for Basic authentication access to Exchange Online API's for Office 365 customers, it says 'Today, we are announcing that on October 13th, 2020 we will stop supporting and retire Basic Authentication for Exchange Active Sync (EAS), Post Office Protocol (POP), Internet Message Access Protocol.
The article was updated on February 25, 2021
Due to the Covid-19 pandemic, there was a huge change of plans concerning disabling basic authentication in Microsoft 365 (for connections to Exchange Online). The complete shutdown has been postponed indefinitely. While it gives organizations much more time to prepare, it’s a good idea to get tenants ready before the actual deadline. Continue reading this article to learn more about basic authentication in Microsoft 365, how to block it on your own and when exactly it will be disabled.
Timeline for disabling basic authentication in Office 365
Initially, basic authentication’s demise was scheduled for October 2020. In April 2020, the date was postponed. There was more than one reason for the delay. One of the reasons was Covid-19 and its impact on businesses. Another important factor was that many organizations still actively used basic authentication in their tenants.
As announced on the Exchange Team Blog in February 2021, it turns out that the complete disabling has been rescheduled once again.
The most important dates connected to disabling basic authentication are as follows.
- October 22, 2019 – Security Defaults are now turned on by default for all new users. Security Defaults block all legacy authentication protocols.
- October 13, 2020 – the initial date for disabling basic authentication in Exchange Online for all tenants. (Postponed)
- October 2020 – basic auth will be disabled for tenants which do not effectively use it.
- Second half of 2021 – that’s when basic authentication will be disabled for all tenants. More precise date is yet to be announced. (Postponed)
- February 2021 – Microsoft announces that basic authentication will not be blocked for now for any protocols that a tenant is using. However, basic auth will be blocked for the unused protocols, with a warning issued 30 days beforehand in the Microsoft 365 Message Center in your tenant.
- The complete shutdown of basic authentication for connections to Exchange Online will be announced at least 12 months before it happens. That should be more than enough to tie up all the loose ends.
Rescheduling the end of support date for basic authentication proves that blocking legacy authentication protocol is quite complex. It also means that now it’s more important than ever to know how to disable basic authentication on your own and what are the consequences of doing so. Read on to learn everything about it.
Impact on organization and users
Each and every app, program or service that connects to Microsoft 365, needs to authenticate itself. Once basic authentication is disabled, all applications which use this legacy authentication protocol to access Exchange Online will stop working. You definitely need to take some action if anyone in your company still uses:
- Outlook 2010 and older – with basic authentication disabled, those email clients will be unable to connect to Microsoft 365.
- Outlook 2013 – enabling OAuth in Outlook 2013 requires some changes to be made in the registry.
- Outlook 2011 for Mac – just as in the case of Outlook 2010, it does not support modern authentication.
- Remote PowerShell – you will need to use the modern Exchange Online module V2 (learn how to connect remotely to your tenant using this module). If you have any unattended scripts in which you use basic authentication to establish a connection to Exchange Online, they will stop working.
- Any third-party app, add-in or mobile email client which doesn’t support modern authentication.
Some tenants may already be qualified for disabling basic authentication. In some cases, IT departments will need to update or upgrade software on multiple workstations.
The bottom line is that any Microsoft 365 administrator should prepare for the upcoming changes. If you were never interested in how authentication works, now is the time to take a quick look at some of the key differences between basic and modern authentication.
Basic authentication vs modern authentication
Although the forced switch from basic authentication to more modern security measures might be troublesome, it is a welcome change. Modern authentication, which is based on ADAL (Active Directory Authentication Library) and OAuth 2.0, offers a more secure method of authentication. To put it in simple terms, basic authentication requires each app, service or add-in to pass credentials – login and password – with each request. It means that those applications store users’ or admins’ credentials somewhere in their settings. This opens many possibilities for attackers. What’s more, basic auth doesn’t support scoping or grading permissions, so every app which connects with the basic auth protocol, gains potential access to all data a certain user has access to. In the current day and age, the best security and privacy-related practice is to allow access only to data and resources required for an application to work, nothing more. The impact will be even greater if a leaked password is used in other places as well.
Modern authentication doesn’t let apps save Microsoft 365 account credentials. In order for an app/service/client to be authenticated, a user needs to log in to their account using the standard Microsoft 365 login experience and accept an app’s request to access their account. Access is granted thanks to tokens, which have a set lifetime. Tokens give a strictly defined permission scope, which needs to be accepted by the signed in user. Finally, modern authentication enables the use of multi-factor authentication (MFA), which adds yet another security layer to your tenant.
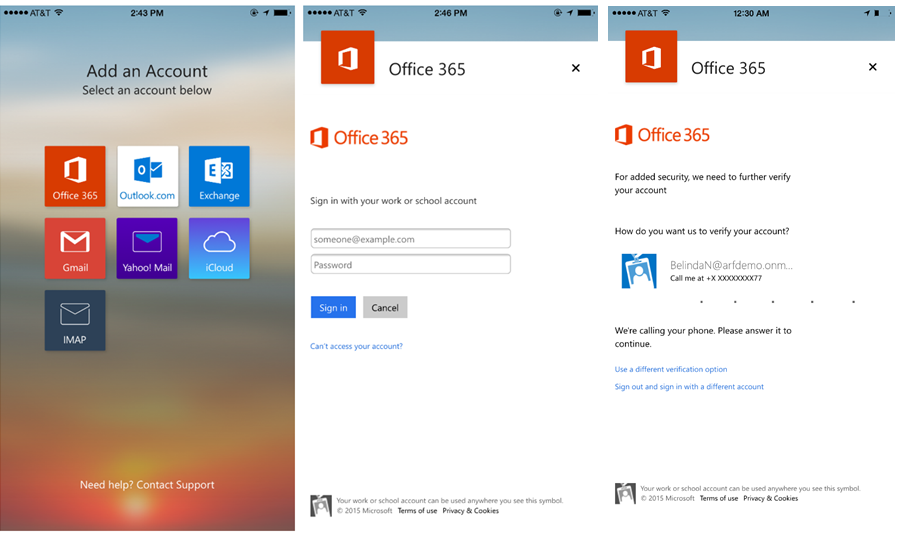
Your organization may not need to continue using basic authentication. To make sure, you need to find out which applications are used to sign in to your tenant. You can use Azure Active Directory for that purpose.
Checking applications which sign in to Azure AD
You can check sign-ins to your Microsoft 365 tenant in the Azure Active Directory admin center by going to Azure Active Directory > Monitoring > Sign-ins (or by using this link). The Sign-ins page allows you to check which applications are used to connect to your Microsoft 365 organization, who connects, where from, and much more:
When you click any record, you will be able to learn more about the sign-in attempt. It includes information about the device used to sign in and authentication details.
How to disable basic authentication in Office 365
There is more than one way to block basic authentication in Office 365 (Microsoft 365). For example, you can use:
- Security Defaults – turned on by default for all new tenants. This set of security-related settings disables all legacy authentication methods, including basic auth and app passwords. Enabling security defaults might influence some third-party applications you use with your Microsoft 365 tenant.
- Client Access Rules – covered in detail in this article. Client Access Rules allow you to create a very specific rules to allow basic auth in very specific cases. You can, for example, allow basic auth for a certain AD group or IP range used in your HQ.
- Authentication policies – a tool dedicated to blocking basic auth. You can control those policies using PowerShell (Set-AuthenticationPolicy) or the Microsoft 365 admin center. Since the tool is dedicated to blocking basic authentication, I’ll describe some general principles on how to use it below.
To configure authentication policies, go to the Microsoft 365 admin center > Settings > Org settings > Modern authentication or use this link.
In this window, you can choose which protocols should be able to use basic authentication to access your tenant. You can, for example, uncheck Exchange Online PowerShell to make it impossible to use this legacy authentication method to start a remote PowerShell Session to Exchange Online. There is a catch, though. It takes 24 hours for the changes made in this panel to kick in. You can force changes, but it requires using PowerShell.
When I run the Get-AuthenticationPolicy cmdlet, I can see that the changes have already been applied:
Which is ironic, because I’ve used the basic auth method to connect to Exchange Online via PowerShell in the first place.
To force-apply Authentication Policies changes for a single account (in the example below, it will apply them to admin), you can run the following cmdlet:
To apply changes to all mailboxes, run the following code:
After doing so, if you used the basic auth method to start a remote PowerShell session, trying to run any Exchange Online cmdlet should make the login pop-up window to appear:
Now, even if you insert correct credentials, the PowerShell console should display the access denied message:
Since the logon attempt wasn’t successful, it will not appear on the Microsoft Azure Sign-ins page.
Basic authentication in Office 365 vs CodeTwo software
Here at CodeTwo, we believe that security should always be a priority. That’s why all our solutions for Microsoft 365 support modern authentication. So, if you’re using our tools for email signature management, backup or migration purposes, you can rest assured that when basic authentication is disabled, they will continue to work without issues. And if you don’t know our products, take a look below for a quick overview:
Office 365 Authentication Methods
- CodeTwo Email Signatures for Office 365 – lets you manage email signatures in your Microsoft 365 organization. In just a few moments, you can design and deploy rules which add professionally branded email signatures for emails sent from any email client and device.
- CodeTwo Backup for Office 365 – secures your Microsoft 365 organization by creating a continuous backup of your organization’s emails, documents and other resources. Backed-up data can later be quickly discovered and restored to its original location or the location of your choice.
- CodeTwo Office 365 Migration – lets you easily and securely migrate data between Microsoft 365 tenants, or from on-premises Exchange to Microsoft 365. You can simplify your migration process and let the tool handle most of the work.
- CodeTwo User Photos for Office 365 – a freeware tool which lets you manage user photos in Microsoft 365. The tool allows you to quickly and easily import and export profile pictures for all users, without the need to use any scripts. Those photos are displayed in Microsoft 365 settings, Outlook, Teams, Outlook on the web, and more.
If you are using CodeTwo Backup for Office 365 or CodeTwo Office 365 Migration, make sure to update it to the latest version. This way, you will get the most secure and reliable experience.
-->Office 365 requires connectivity to the Internet. The endpoints below should be reachable for customers using Office 365 plans, including Government Community Cloud (GCC).
Office 365 Worldwide (+GCC) | Office 365 operated by 21 Vianet | Office 365 Germany | Office 365 U.S. Government DoD | Office 365 U.S. Government GCC High |
| Last updated: 03/01/2021 - Change Log subscription | Download: all required and optional destinations in one JSON formatted list. | Use: our proxy PAC files |
Start with Managing Office 365 endpoints to understand our recommendations for managing network connectivity using this data. Endpoints data is updated as needed at the beginning of each month with new IP Addresses and URLs published 30 days in advance of being active. This allows for customers who do not yet have automated updates to complete their processes before new connectivity is required. Endpoints may also be updated during the month if needed to address support escalations, security incidents, or other immediate operational requirements. The data shown on this page below is all generated from the REST-based web services. If you are using a script or a network device to access this data, you should go to the Web service directly.
Endpoint data below lists requirements for connectivity from a user's machine to Office 365. It does not include network connections from Microsoft into a customer network, sometimes called hybrid or inbound network connections. See Additional endpoints for more information.
The endpoints are grouped into four service areas. The first three service areas can be independently selected for connectivity. The fourth service area is a common dependency (called Microsoft 365 Common and Office) and must always have network connectivity.
Data columns shown are:
ID: The ID number of the row, also known as an endpoint set. This ID is the same as is returned by the web service for the endpoint set.
Category: Shows whether the endpoint set is categorized as 'Optimize', 'Allow', or 'Default'. You can read about these categories and guidance for management of them at New Office 365 endpoint categories. This column also lists which endpoint sets are required to have network connectivity. For endpoint sets which are not required to have network connectivity, we provide notes in this field to indicate what functionality would be missing if the endpoint set is blocked. If you are excluding an entire service area, the endpoint sets listed as required do not require connectivity.
ER: This is Yes if the endpoint set is supported over Azure ExpressRoute with Office 365 route prefixes. The BGP community that includes the route prefixes shown aligns with the service area listed. When ER is No, this means that ExpressRoute is not supported for this endpoint set. However, it should not be assumed that no routes are advertised for an endpoint set where ER is No.
Addresses: Lists the FQDNs or wildcard domain names and IP Address ranges for the endpoint set. Note that an IP Address range is in CIDR format and may include many individual IP Addresses in the specified network.
Ports: Lists the TCP or UDP ports that are combined with the Addresses to form the network endpoint. You may notice some duplication in IP Address ranges where there are different ports listed.
Exchange Online
| ID | Category | ER | Addresses | Ports |
|---|---|---|---|---|
| 1 | Optimize Required | Yes | outlook.office.com, outlook.office365.com13.107.6.152/31, 13.107.18.10/31, 13.107.128.0/22, 23.103.160.0/20, 40.96.0.0/13, 40.104.0.0/15, 52.96.0.0/14, 131.253.33.215/32, 132.245.0.0/16, 150.171.32.0/22, 204.79.197.215/32, 2603:1006::/40, 2603:1016::/36, 2603:1026::/36, 2603:1036::/36, 2603:1046::/36, 2603:1056::/36, 2603:1096::/38, 2603:1096:400::/40, 2603:1096:600::/40, 2603:1096:a00::/39, 2603:1096:c00::/40, 2603:10a6:200::/40, 2603:10a6:400::/40, 2603:10a6:600::/40, 2603:10a6:800::/40, 2603:10d6:200::/40, 2620:1ec:4::152/128, 2620:1ec:4::153/128, 2620:1ec:c::10/128, 2620:1ec:c::11/128, 2620:1ec:d::10/128, 2620:1ec:d::11/128, 2620:1ec:8f0::/46, 2620:1ec:900::/46, 2620:1ec:a92::152/128, 2620:1ec:a92::153/128, 2a01:111:f400::/48 | TCP: 443, 80 |
| 2 | Allow Required | Yes | smtp.office365.com13.107.6.152/31, 13.107.18.10/31, 13.107.128.0/22, 23.103.160.0/20, 40.96.0.0/13, 40.104.0.0/15, 52.96.0.0/14, 131.253.33.215/32, 132.245.0.0/16, 150.171.32.0/22, 204.79.197.215/32, 2603:1006::/40, 2603:1016::/36, 2603:1026::/36, 2603:1036::/36, 2603:1046::/36, 2603:1056::/36, 2603:1096::/38, 2603:1096:400::/40, 2603:1096:600::/40, 2603:1096:a00::/39, 2603:1096:c00::/40, 2603:10a6:200::/40, 2603:10a6:400::/40, 2603:10a6:600::/40, 2603:10a6:800::/40, 2603:10d6:200::/40, 2620:1ec:4::152/128, 2620:1ec:4::153/128, 2620:1ec:c::10/128, 2620:1ec:c::11/128, 2620:1ec:d::10/128, 2620:1ec:d::11/128, 2620:1ec:8f0::/46, 2620:1ec:900::/46, 2620:1ec:a92::152/128, 2620:1ec:a92::153/128, 2a01:111:f400::/48 | TCP: 587 |
| 3 | Default Required | No | r1.res.office365.com, r3.res.office365.com, r4.res.office365.com | TCP: 443, 80 |
| 5 | Allow Optional Notes: Exchange Online IMAP4 migration | Yes | *.outlook.office.com, outlook.office365.com13.107.6.152/31, 13.107.18.10/31, 13.107.128.0/22, 23.103.160.0/20, 40.96.0.0/13, 40.104.0.0/15, 52.96.0.0/14, 131.253.33.215/32, 132.245.0.0/16, 150.171.32.0/22, 204.79.197.215/32, 2603:1006::/40, 2603:1016::/36, 2603:1026::/36, 2603:1036::/36, 2603:1046::/36, 2603:1056::/36, 2603:1096::/38, 2603:1096:400::/40, 2603:1096:600::/40, 2603:1096:a00::/39, 2603:1096:c00::/40, 2603:10a6:200::/40, 2603:10a6:400::/40, 2603:10a6:600::/40, 2603:10a6:800::/40, 2603:10d6:200::/40, 2620:1ec:4::152/128, 2620:1ec:4::153/128, 2620:1ec:c::10/128, 2620:1ec:c::11/128, 2620:1ec:d::10/128, 2620:1ec:d::11/128, 2620:1ec:8f0::/46, 2620:1ec:900::/46, 2620:1ec:a92::152/128, 2620:1ec:a92::153/128, 2a01:111:f400::/48 | TCP: 143, 993 |
| 6 | Allow Optional Notes: Exchange Online POP3 migration | Yes | *.outlook.office.com, outlook.office365.com13.107.6.152/31, 13.107.18.10/31, 13.107.128.0/22, 23.103.160.0/20, 40.96.0.0/13, 40.104.0.0/15, 52.96.0.0/14, 131.253.33.215/32, 132.245.0.0/16, 150.171.32.0/22, 204.79.197.215/32, 2603:1006::/40, 2603:1016::/36, 2603:1026::/36, 2603:1036::/36, 2603:1046::/36, 2603:1056::/36, 2603:1096::/38, 2603:1096:400::/40, 2603:1096:600::/40, 2603:1096:a00::/39, 2603:1096:c00::/40, 2603:10a6:200::/40, 2603:10a6:400::/40, 2603:10a6:600::/40, 2603:10a6:800::/40, 2603:10d6:200::/40, 2620:1ec:4::152/128, 2620:1ec:4::153/128, 2620:1ec:c::10/128, 2620:1ec:c::11/128, 2620:1ec:d::10/128, 2620:1ec:d::11/128, 2620:1ec:8f0::/46, 2620:1ec:900::/46, 2620:1ec:a92::152/128, 2620:1ec:a92::153/128, 2a01:111:f400::/48 | TCP: 995 |
| 8 | Default Required | No | *.outlook.com, *.outlook.office.com, attachments.office.net | TCP: 443, 80 |
| 9 | Allow Required | Yes | *.protection.outlook.com40.92.0.0/15, 40.107.0.0/16, 52.100.0.0/14, 52.238.78.88/32, 104.47.0.0/17, 2a01:111:f403::/48 | TCP: 443 |
| 10 | Allow Required | Yes | *.mail.protection.outlook.com40.92.0.0/15, 40.107.0.0/16, 52.100.0.0/14, 104.47.0.0/17, 2a01:111:f400::/48, 2a01:111:f403::/48 | TCP: 25 |
| 154 | Default Required | No | autodiscover.<tenant>.onmicrosoft.com | TCP: 443, 80 |
SharePoint Online and OneDrive for Business
| ID | Category | ER | Addresses | Ports |
|---|---|---|---|---|
| 31 | Optimize Required | Yes | <tenant>.sharepoint.com, <tenant>-my.sharepoint.com13.107.136.0/22, 40.108.128.0/17, 52.104.0.0/14, 104.146.128.0/17, 150.171.40.0/22, 2620:1ec:8f8::/46, 2620:1ec:908::/46, 2a01:111:f402::/48 | TCP: 443, 80 |
| 32 | Default Optional Notes: OneDrive for Business: supportability, telemetry, APIs, and embedded email links | No | *.log.optimizely.com, ssw.live.com, storage.live.com | TCP: 443 |
| 33 | Default Optional Notes: SharePoint Hybrid Search - Endpoint to SearchContentService where the hybrid crawler feeds documents | No | *.search.production.apac.trafficmanager.net, *.search.production.emea.trafficmanager.net, *.search.production.us.trafficmanager.net | TCP: 443 |
| 35 | Default Required | No | *.wns.windows.com, admin.onedrive.com, officeclient.microsoft.com | TCP: 443, 80 |
| 36 | Default Required | No | g.live.com, oneclient.sfx.ms | TCP: 443, 80 |
| 37 | Default Required | No | *.sharepointonline.com, cdn.sharepointonline.com, privatecdn.sharepointonline.com, publiccdn.sharepointonline.com, spoprod-a.akamaihd.net, static.sharepointonline.com | TCP: 443, 80 |
| 38 | Default Optional Notes: SharePoint Online: auxiliary URLs | No | prod.msocdn.com, watson.telemetry.microsoft.com | TCP: 443, 80 |
| 39 | Default Required | No | *.svc.ms, <tenant>-files.sharepoint.com, <tenant>-myfiles.sharepoint.com | TCP: 443, 80 |
Skype for Business Online and Microsoft Teams
| ID | Category | ER | Addresses | Ports |
|---|---|---|---|---|
| 11 | Optimize Required | Yes | 13.107.64.0/18, 52.112.0.0/14, 52.120.0.0/14 | UDP: 3478, 3479, 3480, 3481 |
| 12 | Allow Required | Yes | *.lync.com, *.teams.microsoft.com, teams.microsoft.com13.107.64.0/18, 52.112.0.0/14, 52.120.0.0/14, 52.238.119.141/32, 52.244.160.207/32, 2603:1027::/48, 2603:1037::/48, 2603:1047::/48, 2603:1057::/48, 2620:1ec:6::/48, 2620:1ec:40::/42 | TCP: 443, 80 |
| 13 | Allow Required | Yes | *.broadcast.skype.com, broadcast.skype.com13.107.64.0/18, 52.112.0.0/14, 52.120.0.0/14, 52.238.119.141/32, 52.244.160.207/32, 2603:1027::/48, 2603:1037::/48, 2603:1047::/48, 2603:1057::/48, 2620:1ec:6::/48, 2620:1ec:40::/42 | TCP: 443 |
| 15 | Default Required | No | *.sfbassets.com, *.urlp.sfbassets.com, skypemaprdsitus.trafficmanager.net | TCP: 443, 80 |
| 16 | Default Required | No | *.keydelivery.mediaservices.windows.net, *.msecnd.net, *.streaming.mediaservices.windows.net, ajax.aspnetcdn.com, mlccdn.blob.core.windows.net | TCP: 443 |
| 17 | Default Required | No | aka.ms, amp.azure.net | TCP: 443 |
| 18 | Default Optional Notes: Federation with Skype and public IM connectivity: Contact picture retrieval | No | *.users.storage.live.com | TCP: 443 |
| 19 | Default Optional Notes: Applies only to those who deploy the Conference Room Systems | No | *.adl.windows.com | TCP: 443, 80 |
| 22 | Allow Optional Notes: Teams: Messaging interop with Skype for Business | Yes | *.skypeforbusiness.com13.107.64.0/18, 52.112.0.0/14, 52.120.0.0/14, 52.238.119.141/32, 52.244.160.207/32, 2603:1027::/48, 2603:1037::/48, 2603:1047::/48, 2603:1057::/48, 2620:1ec:6::/48, 2620:1ec:40::/42 | TCP: 443 |
| 26 | Default Required | No | *.msedge.net, compass-ssl.microsoft.com | TCP: 443 |
| 27 | Default Required | No | *.mstea.ms, *.secure.skypeassets.com, mlccdnprod.azureedge.net, videoplayercdn.osi.office.net | TCP: 443 |
| 29 | Default Optional Notes: Yammer third-party integration | No | *.tenor.com | TCP: 443, 80 |
| 127 | Default Required | No | *.skype.com | TCP: 443, 80 |
Microsoft 365 Common and Office Online
| ID | Category | ER | Addresses | Ports |
|---|---|---|---|---|
| 40 | Default Optional Notes: Office 365 Video CDNs | No | ajax.aspnetcdn.com, r3.res.outlook.com, spoprod-a.akamaihd.net | TCP: 443 |
| 41 | Default Optional Notes: Microsoft Stream | No | *.microsoftstream.com, amp.azure.net, s0.assets-yammer.com, vortex.data.microsoft.com | TCP: 443 |
| 42 | Default Optional Notes: Microsoft Stream CDN | No | amsglob0cdnstream13.azureedge.net, amsglob0cdnstream14.azureedge.net | TCP: 443 |
| 43 | Default Optional Notes: Microsoft Stream 3rd party integration (including CDNs) | No | nps.onyx.azure.net | TCP: 443 |
| 44 | Default Optional Notes: Microsoft Stream - unauthenticated | No | *.azureedge.net, *.media.azure.net, *.streaming.mediaservices.windows.net | TCP: 443 |
| 45 | Default Optional Notes: Office 365 Video | No | *.keydelivery.mediaservices.windows.net, *.streaming.mediaservices.windows.net | TCP: 443 |
| 46 | Allow Required | Yes | *.officeapps.live.com, *.online.office.com, office.live.com13.107.6.171/32, 13.107.140.6/32, 52.108.0.0/14, 52.238.106.116/32, 52.244.37.168/32, 52.244.203.72/32, 52.244.207.172/32, 52.244.223.198/32, 52.247.150.191/32, 2603:1010:2::cb/128, 2603:1010:200::c7/128, 2603:1020:200::682f:a0fd/128, 2603:1020:201:9::c6/128, 2603:1020:600::a1/128, 2603:1020:700::a2/128, 2603:1020:800:2::6/128, 2603:1020:900::8/128, 2603:1030:7::749/128, 2603:1030:800:5::bfee:ad3c/128, 2603:1030:f00::17/128, 2603:1030:1000::21a/128, 2603:1040:200::4f3/128, 2603:1040:401::762/128, 2603:1040:601::60f/128, 2603:1040:a01::1e/128, 2603:1040:c01::28/128, 2603:1040:e00:1::2f/128, 2603:1040:f00::1f/128, 2603:1050:1::cd/128, 2620:1ec:8fc::6/128, 2620:1ec:a92::171/128, 2a01:111:f100:2000::a83e:3019/128, 2a01:111:f100:2002::8975:2d79/128, 2a01:111:f100:2002::8975:2da8/128, 2a01:111:f100:7000::6fdd:6cd5/128, 2a01:111:f100:a004::bfeb:88cf/128 | TCP: 443, 80 |
| 47 | Default Required | No | *.cdn.office.net, contentstorage.osi.office.net | TCP: 443 |
| 49 | Default Required | No | *.onenote.com | TCP: 443 |
| 50 | Default Optional Notes: OneNote notebooks (wildcards) | No | *.microsoft.com, *.msecnd.net, *.office.net | TCP: 443 |
| 51 | Default Required | No | *cdn.onenote.net | TCP: 443 |
| 52 | Default Optional Notes: OneNote 3rd party supporting services and CDNs | No | ad.atdmt.com, s.ytimg.com, www.youtube.com | TCP: 443 |
| 53 | Default Required | No | ajax.aspnetcdn.com, apis.live.net, cdn.optimizely.com, officeapps.live.com, www.onedrive.com | TCP: 443 |
| 56 | Allow Required | Yes | *.msftidentity.com, *.msidentity.com, account.activedirectory.windowsazure.com, accounts.accesscontrol.windows.net, adminwebservice.microsoftonline.com, api.passwordreset.microsoftonline.com, autologon.microsoftazuread-sso.com, becws.microsoftonline.com, clientconfig.microsoftonline-p.net, companymanager.microsoftonline.com, device.login.microsoftonline.com, graph.microsoft.com, graph.windows.net, login.microsoft.com, login.microsoftonline.com, login.microsoftonline-p.com, login.windows.net, logincert.microsoftonline.com, loginex.microsoftonline.com, login-us.microsoftonline.com, nexus.microsoftonline-p.com, passwordreset.microsoftonline.com, provisioningapi.microsoftonline.com20.190.128.0/18, 40.126.0.0/18, 2603:1006:2000::/48, 2603:1007:200::/48, 2603:1016:1400::/48, 2603:1017::/48, 2603:1026:3000::/48, 2603:1027:1::/48, 2603:1036:3000::/48, 2603:1037:1::/48, 2603:1046:2000::/48, 2603:1047:1::/48, 2603:1056:2000::/48, 2603:1057:2::/48 | TCP: 443, 80 |
| 59 | Default Required | No | *.hip.live.com, *.microsoftonline.com, *.microsoftonline-p.com, *.msauth.net, *.msauthimages.net, *.msecnd.net, *.msftauth.net, *.msftauthimages.net, *.phonefactor.net, enterpriseregistration.windows.net, management.azure.com, policykeyservice.dc.ad.msft.net | TCP: 443, 80 |
| 64 | Allow Required | Yes | *.compliance.microsoft.com, *.manage.office.com, *.protection.office.com, *.security.microsoft.com, compliance.microsoft.com, manage.office.com, protection.office.com, security.microsoft.com13.80.125.22/32, 13.91.91.243/32, 13.107.6.156/31, 13.107.7.190/31, 13.107.9.156/31, 40.81.156.154/32, 40.90.218.198/32, 52.108.0.0/14, 52.174.56.180/32, 52.183.75.62/32, 52.184.165.82/32, 104.42.230.91/32, 157.55.145.0/25, 157.55.155.0/25, 157.55.227.192/26, 2603:1006:1400::/40, 2603:1010:2:2::a/128, 2603:1016:2400::/40, 2603:1020:400::26/128, 2603:1020:600::12f/128, 2603:1020:600::1f0/128, 2603:1020:800:2::45/128, 2603:1026:2400::/40, 2603:1030:7:5::25/128, 2603:1036:2400::/40, 2603:1040:400::5e/128, 2603:1040:601::2/128, 2603:1046:1400::/40, 2603:1056:1400::/40, 2a01:111:200a:a::/64, 2a01:111:2035:8::/64, 2a01:111:f100:1002::4134:c440/128, 2a01:111:f100:2000::a83e:33a8/128, 2a01:111:f100:2002::8975:2d98/128, 2a01:111:f100:3000::a83e:1884/128, 2a01:111:f100:3002::8987:3552/128, 2a01:111:f100:4002::9d37:c021/128, 2a01:111:f100:4002::9d37:c3de/128, 2a01:111:f100:6000::4134:a6c7/128, 2a01:111:f100:6000::4134:b84b/128, 2a01:111:f100:7000::6fdd:5245/128, 2a01:111:f100:7000::6fdd:6fc4/128, 2a01:111:f100:8000::4134:941b/128, 2a01:111:f100:9001::1761:914f/128, 2a01:111:f406:1::/64, 2a01:111:f406:c00::/64, 2a01:111:f406:1004::/64, 2a01:111:f406:1805::/64, 2a01:111:f406:3404::/64, 2a01:111:f406:8000::/64, 2a01:111:f406:8801::/64, 2a01:111:f406:a003::/64 | TCP: 443 |
| 65 | Allow Required | Yes | *.portal.cloudappsecurity.com, account.office.net, admin.microsoft.com, home.office.com, portal.office.com, www.office.com13.80.125.22/32, 13.91.91.243/32, 13.107.6.156/31, 13.107.7.190/31, 13.107.9.156/31, 40.81.156.154/32, 40.90.218.198/32, 52.108.0.0/14, 52.174.56.180/32, 52.183.75.62/32, 52.184.165.82/32, 104.42.230.91/32, 157.55.145.0/25, 157.55.155.0/25, 157.55.227.192/26, 2603:1006:1400::/40, 2603:1010:2:2::a/128, 2603:1016:2400::/40, 2603:1020:400::26/128, 2603:1020:600::12f/128, 2603:1020:600::1f0/128, 2603:1020:800:2::45/128, 2603:1026:2400::/40, 2603:1030:7:5::25/128, 2603:1036:2400::/40, 2603:1040:400::5e/128, 2603:1040:601::2/128, 2603:1046:1400::/40, 2603:1056:1400::/40, 2a01:111:200a:a::/64, 2a01:111:2035:8::/64, 2a01:111:f100:1002::4134:c440/128, 2a01:111:f100:2000::a83e:33a8/128, 2a01:111:f100:2002::8975:2d98/128, 2a01:111:f100:3000::a83e:1884/128, 2a01:111:f100:3002::8987:3552/128, 2a01:111:f100:4002::9d37:c021/128, 2a01:111:f100:4002::9d37:c3de/128, 2a01:111:f100:6000::4134:a6c7/128, 2a01:111:f100:6000::4134:b84b/128, 2a01:111:f100:7000::6fdd:5245/128, 2a01:111:f100:7000::6fdd:6fc4/128, 2a01:111:f100:8000::4134:941b/128, 2a01:111:f100:9001::1761:914f/128, 2a01:111:f406:1::/64, 2a01:111:f406:c00::/64, 2a01:111:f406:1004::/64, 2a01:111:f406:1805::/64, 2a01:111:f406:3404::/64, 2a01:111:f406:8000::/64, 2a01:111:f406:8801::/64, 2a01:111:f406:a003::/64 | TCP: 443, 80 |
| 66 | Default Required | No | suite.office.net | TCP: 443 |
| 67 | Default Optional Notes: Security and Compliance Center eDiscovery export | No | *.blob.core.windows.net | TCP: 443 |
| 68 | Default Optional Notes: Portal and shared: 3rd party office integration. (including CDNs) | No | *.helpshift.com, *.localytics.com, analytics.localytics.com, api.localytics.com, connect.facebook.net, firstpartyapps.oaspapps.com, outlook.uservoice.com, prod.firstpartyapps.oaspapps.com.akadns.net, rink.hockeyapp.net, sdk.hockeyapp.net, telemetryservice.firstpartyapps.oaspapps.com, web.localytics.com, webanalytics.localytics.com, wus-firstpartyapps.oaspapps.com | TCP: 443 |
| 69 | Default Required | No | *.aria.microsoft.com, *.events.data.microsoft.com | TCP: 443 |
| 70 | Default Required | No | *.o365weve.com, amp.azure.net, appsforoffice.microsoft.com, assets.onestore.ms, auth.gfx.ms, c1.microsoft.com, contentstorage.osi.office.net, dgps.support.microsoft.com, docs.microsoft.com, msdn.microsoft.com, platform.linkedin.com, prod.msocdn.com, shellprod.msocdn.com, support.content.office.net, support.microsoft.com, technet.microsoft.com, videocontent.osi.office.net, videoplayercdn.osi.office.net | TCP: 443 |
| 71 | Default Required | No | *.office365.com | TCP: 443 |
| 72 | Default Optional Notes: Azure Rights Management (RMS) with Office 2010 clients | No | *.cloudapp.net | TCP: 443 |
| 73 | Default Required | No | *.aadrm.com, *.azurerms.com, *.informationprotection.azure.com, ecn.dev.virtualearth.net, informationprotection.hosting.portal.azure.net | TCP: 443 |
| 74 | Default Optional Notes: Remote Connectivity Analyzer - Initiate connectivity tests. | No | testconnectivity.microsoft.com | TCP: 443, 80 |
| 75 | Default Optional Notes: Graph.windows.net, Office 365 Management Pack for Operations Manager, SecureScore, Azure AD Device Registration, Forms, StaffHub, Application Insights, captcha services | No | *.hockeyapp.net, *.sharepointonline.com, cdn.forms.office.net, dc.applicationinsights.microsoft.com, dc.services.visualstudio.com, forms.microsoft.com, mem.gfx.ms, office365servicehealthcommunications.cloudapp.net, osiprod-cus-daffodil-signalr-00.service.signalr.net, osiprod-neu-daffodil-signalr-00.service.signalr.net, osiprod-weu-daffodil-signalr-00.service.signalr.net, osiprod-wus-daffodil-signalr-00.service.signalr.net, signup.microsoft.com, staffhub.ms, staffhub.uservoice.com, staffhubweb.azureedge.net, watson.telemetry.microsoft.com | TCP: 443 |
| 77 | Allow Required | Yes | portal.microsoftonline.com13.107.6.171/32, 13.107.140.6/32, 52.108.0.0/14, 52.238.106.116/32, 52.244.37.168/32, 52.244.203.72/32, 52.244.207.172/32, 52.244.223.198/32, 52.247.150.191/32, 2603:1010:2::cb/128, 2603:1010:200::c7/128, 2603:1020:200::682f:a0fd/128, 2603:1020:201:9::c6/128, 2603:1020:600::a1/128, 2603:1020:700::a2/128, 2603:1020:800:2::6/128, 2603:1020:900::8/128, 2603:1030:7::749/128, 2603:1030:800:5::bfee:ad3c/128, 2603:1030:f00::17/128, 2603:1030:1000::21a/128, 2603:1040:200::4f3/128, 2603:1040:401::762/128, 2603:1040:601::60f/128, 2603:1040:a01::1e/128, 2603:1040:c01::28/128, 2603:1040:e00:1::2f/128, 2603:1040:f00::1f/128, 2603:1050:1::cd/128, 2620:1ec:8fc::6/128, 2620:1ec:a92::171/128, 2a01:111:f100:2000::a83e:3019/128, 2a01:111:f100:2002::8975:2d79/128, 2a01:111:f100:2002::8975:2da8/128, 2a01:111:f100:7000::6fdd:6cd5/128, 2a01:111:f100:a004::bfeb:88cf/128 | TCP: 443 |
| 78 | Default Optional Notes: Some Office 365 features require endpoints within these domains (including CDNs). Many specific FQDNs within these wildcards have been published recently as we work to either remove or better explain our guidance relating to these wildcards. | No | *.microsoft.com, *.msocdn.com, *.office.net, *.onmicrosoft.com | TCP: 443, 80 |
| 79 | Default Required | No | o15.officeredir.microsoft.com, officepreviewredir.microsoft.com, officeredir.microsoft.com, r.office.microsoft.com | TCP: 443, 80 |
| 80 | Default Required | No | ocws.officeapps.live.com | TCP: 443 |
| 81 | Default Required | No | odc.officeapps.live.com | TCP: 443, 80 |
| 82 | Default Required | No | roaming.officeapps.live.com | TCP: 443, 80 |
| 83 | Default Required | No | activation.sls.microsoft.com | TCP: 443 |
| 84 | Default Required | No | crl.microsoft.com | TCP: 443, 80 |
| 86 | Default Required | No | office15client.microsoft.com, officeclient.microsoft.com | TCP: 443 |
| 88 | Default Required | No | insertmedia.bing.office.net | TCP: 443, 80 |
| 89 | Default Required | No | go.microsoft.com, support.office.com | TCP: 443, 80 |
| 91 | Default Required | No | ajax.aspnetcdn.com | TCP: 443, 80 |
| 92 | Default Required | No | officecdn.microsoft.com, officecdn.microsoft.com.edgesuite.net | TCP: 443, 80 |
| 93 | Default Optional Notes: ProPlus: auxiliary URLs | No | *.virtualearth.net, ajax.microsoft.com, c.bing.net, excelbingmap.firstpartyapps.oaspapps.com, excelcs.officeapps.live.com, ocos-office365-s2s.msedge.net, omextemplates.content.office.net, peoplegraph.firstpartyapps.oaspapps.com, pptcs.officeapps.live.com, tse1.mm.bing.net, uci.officeapps.live.com, watson.microsoft.com, wikipedia.firstpartyapps.oaspapps.com, wordcs.officeapps.live.com, www.bing.com | TCP: 443, 80 |
| 95 | Default Optional Notes: Outlook for Android and iOS | No | *.acompli.net, *.outlookmobile.com | TCP: 443 |
| 96 | Default Optional Notes: Outlook for Android and iOS: Authentication | No | *.manage.microsoft.com, api.office.com, go.microsoft.com, login.windows-ppe.net, secure.aadcdn.microsoftonline-p.com, vortex.data.microsoft.com | TCP: 443 |
| 97 | Default Optional Notes: Outlook for Android and iOS: Consumer Outlook.com and OneDrive integration | No | account.live.com, apis.live.net, auth.gfx.ms, login.live.com | TCP: 443 |
| 98 | Default Optional Notes: Outlook for Android and iOS: Google integration | No | accounts.google.com, mail.google.com, www.googleapis.com | TCP: 443 |
| 99 | Default Optional Notes: Outlook for Android and iOS: Yahoo integration | No | api.login.yahoo.com, social.yahooapis.com | TCP: 443 |
| 100 | Default Optional Notes: Outlook for Android and iOS: DropBox integration | No | api.dropboxapi.com, www.dropbox.com | TCP: 443 |
| 101 | Default Optional Notes: Outlook for Android and iOS: Box integration | No | app.box.com | TCP: 443 |
| 102 | Default Optional Notes: Outlook for Android and iOS: Facebook integration | No | graph.facebook.com, m.facebook.com | TCP: 443 |
| 103 | Default Optional Notes: Outlook for Android and iOS: Evernote integration | No | www.evernote.com | TCP: 443 |
| 105 | Default Optional Notes: Outlook for Android and iOS: Outlook Privacy | No | bit.ly, www.acompli.com | TCP: 443 |
| 106 | Default Optional Notes: Outlook for Android and iOS: User voice integration | No | by.uservoice.com, outlook.uservoice.com | TCP: 443 |
| 109 | Default Optional Notes: Outlook for Android and iOS: Flurry log integration | No | data.flurry.com | TCP: 443 |
| 110 | Default Optional Notes: Outlook for Android and iOS: Adjust integration | No | app.adjust.com | TCP: 443 |
| 111 | Default Optional Notes: Outlook for Android and iOS: Hockey log integration | No | rink.hockeyapp.net, sdk.hockeyapp.net | TCP: 443 |
| 112 | Default Optional Notes: Outlook for Android and iOS: Helpshift integration | No | acompli.helpshift.com | TCP: 443 |
| 113 | Default Optional Notes: Outlook for Android and iOS: Play Store integration (Android only) | No | play.google.com | TCP: 443 |
| 114 | Default Optional Notes: Office Mobile URLs | No | *.appex.bing.com, *.appex-rf.msn.com, *.itunes.apple.com, c.bing.com, c.live.com, cl2.apple.com, d.docs.live.net, directory.services.live.com, docs.live.net, en-us.appex-rf.msn.com, foodanddrink.services.appex.bing.com, office.microsoft.com, partnerservices.getmicrosoftkey.com, sas.office.microsoft.com, signup.live.com, view.atdmt.com, watson.telemetry.microsoft.com, weather.tile.appex.bing.com | TCP: 443, 80 |
| 115 | Default Optional Notes: Outlook for Android and iOS: Meetup integration | No | api.meetup.com, secure.meetup.com | TCP: 443 |
| 116 | Default Optional Notes: Office for iPad URLs | No | account.live.com, auth.gfx.ms, c.bing.com, c.live.com, cl2.apple.com, directory.services.live.com, docs.live.net, en-us.appex-rf.msn.com, foodanddrink.services.appex.bing.com, go.microsoft.com, login.live.com, office.microsoft.com, p100-sandbox.itunes.apple.com, partnerservices.getmicrosoftkey.com, roaming.officeapps.live.com, sas.office.microsoft.com, signup.live.com, view.atdmt.com, watson.telemetry.microsoft.com, weather.tile.appex.bing.com | TCP: 443, 80 |
| 117 | Default Optional Notes: Yammer | No | *.yammer.com, *.yammerusercontent.com | TCP: 443 |
| 118 | Default Optional Notes: Yammer CDN | No | *.assets-yammer.com | TCP: 443 |
| 120 | Default Optional Notes: Planner CDNs | No | ajax.aspnetcdn.com | TCP: 443 |
| 121 | Default Optional Notes: Planner: auxiliary URLs | No | www.outlook.com | TCP: 443, 80 |
| 122 | Default Optional Notes: Sway CDNs | No | eus-www.sway-cdn.com, eus-www.sway-extensions.com, wus-www.sway-cdn.com, wus-www.sway-extensions.com | TCP: 443 |
| 123 | Default Optional Notes: Sway website analytics | No | www.google-analytics.com | TCP: 443 |
| 124 | Default Optional Notes: Sway | No | sway.com, www.sway.com | TCP: 443 |
| 125 | Default Required | No | *.entrust.net, *.geotrust.com, *.omniroot.com, *.public-trust.com, *.symcb.com, *.symcd.com, *.verisign.com, *.verisign.net, apps.identrust.com, cacerts.digicert.com, cert.int-x3.letsencrypt.org, crl.globalsign.com, crl.globalsign.net, crl.identrust.com, crl.microsoft.com, crl3.digicert.com, crl4.digicert.com, isrg.trustid.ocsp.identrust.com, mscrl.microsoft.com, ocsp.digicert.com, ocsp.globalsign.com, ocsp.msocsp.com, ocsp2.globalsign.com, ocspx.digicert.com, secure.globalsign.com, www.digicert.com, www.microsoft.com | TCP: 443, 80 |
| 126 | Default Optional Notes: Connection to the speech service is required for Office Dictation features. If connectivity is not allowed, Dictation will be disabled. | No | officespeech.platform.bing.com | TCP: 443 |
| 128 | Default Required | No | *.config.office.net, *.manage.microsoft.com | TCP: 443 |
| 147 | Default Required | No | *.office.com | TCP: 443, 80 |
| 148 | Default Required | No | cdnprod.myanalytics.microsoft.com, myanalytics.microsoft.com, myanalytics-gcc.microsoft.com | TCP: 443, 80 |
| 149 | Default Required | No | workplaceanalytics.cdn.office.net, workplaceanalytics.office.com | TCP: 443, 80 |
| 150 | Default Optional Notes: Blocking these endpoints will affect the ability to access the Office 365 ProPlus deployment and management features via the portal. | No | *.officeconfig.msocdn.com | TCP: 443 |
| 152 | Default Optional Notes: These endpoints enables the Office Scripts functionality in Office clients available through the Automate tab. This feature can also be disabled through the Office 365 Admin portal. | No | *.microsoftusercontent.com | TCP: 443 |
| 153 | Default Required | No | *.azure-apim.net, *.flow.microsoft.com, *.powerapps.com | TCP: 443 |
| 156 | Default Required | No | activity.windows.com | TCP: 443 |
| 157 | Default Required | No | ocsp.int-x3.letsencrypt.org | TCP: 80 |
Office 365 Authentication Policies
Note
Office 365 Authoritative Vs Internal Relay
For recommendations on Yammer IP addresses and URLs, see Using hard-coded IP addresses for Yammer is not recommended on the Yammer blog.
Office 365 Authorization
Related Topics
